- Sponsored
- Modernization
Cloud IT blind spots pose a growing security threat to agency networks

Mike Stacy is the global director of cloud and information protection at Proofpoint with nearly 17 years’ experience advising organizations on their cloud security programs.
Cloud acquisition strategies — rooted in the Cloud Smart strategy and the President’s Management Agenda IT modernization goals — aim to improve mission delivery and constituent engagement. Those efforts accelerated last year as agencies significantly shifted their investments towards more cloud-based services.

Mike Stacy, Global Director, Cloud and Information Protection, Proofpoint
But the evidence from multiple studies, including our own, suggest that while email-based attacks are still the number one attack vector, the number two threat vector is through cloud-based services. Not only do agencies need to close the visibility gaps in multicloud environments, but they also need a people-centric security approach to better understand both the cyber attacker and the profile types of employees that are being targeted.
In our experience, customers may fall into a false sense of security when they start to operate in the cloud if they view it as a pristine environment. But the reality is that these environments already have malicious actors operating in them, which makes it critical that leaders start to adapt a “threat first” security approach.
Most cloud providers, including those that have received FedRAMP authority to operate, have several built-in security controls. While those services are useful, they are not always effective at blocking many of the rapidly evolving cyberattacks we see today that capitalize on applications operating in multi-cloud environments. Without implementing modern security tools that correlate data and activity moving across cloud environments with threat and risk for contextual visibility and risk-based controls, it makes it harder to identify blind spots and vulnerabilities.
The importance of adopting a ‘threat first’ mindset
Cyberthreat actors are quickly adopting techniques, tools and procedures to exploit these blind spots and infiltrate organization networks.
A large percentage of cloud attacks leverage a combination of phishing, social engineering and credential dumps as reconnaissance tools to breach cloud accounts. Our Proofpoint research found that north of 60% of Microsoft Office 365 tenants which Proofpoint monitors are compromised in any given quarter. That number can tell you a lot. Even if most of those attacks were related to email breaches, there is still a significant portion that aren’t, which points to direct cloud account breaches.
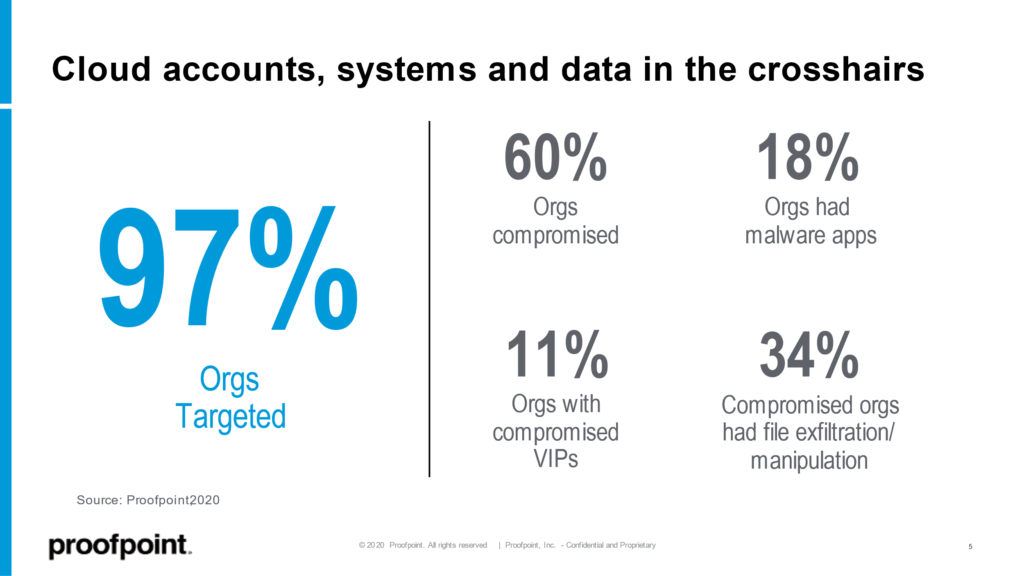
Source: Proofpoint
There are several tactics threat actors are using to breach cloud accounts, for example:
Credential dumps from prior attacks. Threat actors are sharing, trading and selling information and using stolen credentials — in conjunction with automated tools, for example — to directly log into accounts. In fact, that is the most common way that cloud accounts are being breached today. Human error is still the most significant risk factor in security breaches with users using weak or reused passwords.
Shadow IT occurs in most organizations when users deploy cloud-connected apps or services within the enterprise environment. Most often, this isn’t malicious, rather an employee is just trying to perform their job efficiently with the tools they are familiar with. For example, if the agency won’t give a department access to their own SharePoint, maybe a user will use their own Dropbox. Or perhaps an employee wants to create a compelling presentation using services, such as Canva.
Third-party applications and add-ons to tools like Office 365 and G Suite are quickly multiplying; many of which use OAuth authentication, or access tokens, to connect to users’ data. But when the application is not related to an agency’s business at all these applications can introduce supply chain risk into the cloud service is compromised, as we’ve seen examples of this year. Or, maybe a user as their work calendar connected to a smart speaker or virtual assistant and now it (and the company who made it) has visibility into potentially sensitive information, without any data privacy arrangements with that organization.
Organizations may or may not be ok with users access other cloud services, But the question becomes, do your IT and security teams know any of this is happening across the enterprise cloud environment and can they see what data is being exposed there? And unfortunately, SaaS providers haven’t focused on providing good visibility (much less controls) to manage these OAuth authorizations.
People-centric approach to security
From an access perspective, there is no real control over who and how users can access cloud services most of the time, unless you connect every user through a VPN. But the increased demand for hybrid work structures requires a different approach to security and access controls. Improving zero trust security and network monitoring is critical for both on-premises and cloud accesses.
For example, secure access service edge (SASE) — recently renamed SSE by Gartner — is an emerging technology that merges traditional IT infrastructure with cloud services to support a range of users and their locations and it allows for more granular access controls around who needs to get to various services.
Proofpoint’s platform approach to security helps organization take SASE a step further. With our combination of research, tools, capabilities and technology, we provide organizations with the ability to apply risk-based controls based on who is being targeted within the organizations as well as around those applications that are in use across the environment — whether they are authorized or not.
We understand that all users are not created equal and a people-centric security approach to security gives IT the ability to differentiate their security controls based on risk, and then take a specific action to mitigate threats such as initiating browser isolation and data loss prevention (DLP) controls in real-time, without the need to install an agent on the device.
By working with Proofpoint, IT security is taking back control of an area where it may have had limited visibility and is putting real-time controls in place to protect the agency’s people and data.
Learn more about how Proofpoint can help protect federal agencies, and their people, against malicious attackers.






